Ethical Hacker

Ethical Hacker Training
It is an authorized practice of detecting vulnerabilities in a system or application or company’s infrastructure that bypass system security for identifying potential data breaches and threats in the whole network. Ethical hacking also refers to the procedure of taking active security measures to protect systems from hackers or unauthorized persons with malicious intentions for data privacy. In other words, ethical hacking is the procedure of cracking or bypassing security measures implemented by a system to detect data breaches, vulnerabilities, and potential threats. It also helps companies to adopt safe usage and practices of their IT infrastructure. The main work of ethical hackers is that thy hacks the target system before any harmful or stolen information by any unauthorized individuals. It also enables the security team of the company for applying a security patch in the system and successfully eliminate the opening the hackers to enter the system or hack. The main purpose of the ethical hacker is to investigate the network or system for weak points that an unauthorized person may destroy. The ethical hacker also improves the security system to prevent cyber-attacks on the network.
Course Overview
The Ethical Hacker Training helps in understanding the fundamental concepts of this course and clearing the certification exam. This online course also introduces several types of ethical hacking tools and ethical hackers. During the online training, you will learn about the basics of ethical hacking, the importance of ethical hacking, fundamentals of computer Networking, and many more. There are several Ethical Hacker Courses including ethical hacking essentials, ethical hacking for beginners, IBM cybersecurity analyst professional course, penetration testing & ethical hacking, and many more are available as options for trainees to choose the best ethical hacker course that is suitable for their career growth. After getting Ethical Hacker Certification, you will work as an ethical hacker in the best company with a high salary.
The system of the organization enables cyber security engineers for performing several activities to analyze the defense of the network. The main responsibility of an Ethical Hacker is to collect and examine the information to figure out ways for strengthening the security of the network. Thus, companies hire ethical hackers for looking into the vulnerabilities of their whole network and develop solutions in preventing data breaches.
Ethical Hacking Certification Key Features
- Introduction to Ethical Hacking
- Get Ethical Hacking Certification
- Mock tests, Mock interviews
- Real-time projects for practice
- 24/7 support to solve your queries
- Schedule your timing as per your convenience
- One on One sessions
Who should Learn Ethical Hacking?
The ethical hacker course is ideal for those fresher graduates or trainees who want to start a career in the Cyber Security and ethical hacking domain. There are several other professionals who are suitable for this online course are given below –
- IT Security Officers
- Site Administrators
- Technical Support Engineers
- Network Security Officers
- System Analysts
- Network Specialists
Top Hiring Company
Industry Trends
Course curriculum / Syllabus
- Fundamentals of ethical hacking
- What is an information security
- Basic concepts of hacking
- Hacking Frameworks and Methodologies
- Introduction to Information Security Controls
- Elements of Information Security
- Information Security Threats and Attack Vendors
- Information Security Laws and Standards
- Information Security Threat Categories
- What are compliance and laws of cyber security
- Fundamental concepts of system hacking
- Different types of password attacks
- Maintaining Access
- What are Password Recovery Tools
- Kerberos Authentication
- Gaining Access
- Escalating Privileges
- Privilege Escalation by using Dylib Hijacking
- How to protect against privilege escalation
- Overview of Enterprise Information Security Architecture (EISA)
- Network Security Zoning
- Information Security Management Program
- Threat Modelling
- Security Incident and Event Management (SIEM)
- Identify and Access
- Incident Management
- Overview of Identify and Access Management (IAM)
- Description of User Behavior Analytics (UBA)
- Data Backup
- Information Assurance (IA)
- Network Scanning Concepts
- How to use Scanning Tools?
- In-depth knowledge of Scanning Techniques
- Detialing of Scanning Beyond IDS and Firewall
- What is Banner Grabbing?
- Draw Network Diagrams
- Understanding Scanning Pen Testing
- Introduction to Network Scanning
- What is TCP/IP Communication
- How to scan in IPv6 networks
- Overview of Web Applications
- Web Application Architecture
- How to analyze web applications
- Web application hacking methodology
- Attack Access Controls
- Footprint Web Infrastructure
- How to bypass client-side controls
- System Hacking Concepts
- Conepts of Cracking Passwords
- Workings of Privileges
- Executing Applications
- Workings of Hiding Files
- Covering Tracks
- Understanding Penetration Testing
- Introduction to Malware
- How Malware may get into the system in several ways
- Different components of Malware
- Overview of Trojan
- Trojan Horse Construction Kit
- How hackers use and deploy a trojan
- Several types of Trojans
- Concepts of viruses
- Different stages of Virus
- Anti-Virus Sensor Systems
- Overview of Malware Analysis
- Overview of Vulnerability assessment
- Several types of vulnerability assessment
- Vulnerability classification
- Vulnerability-Management Life Cycle
- How to select a vulnerability tool
- Different types of Vulnerability Tools
- Social Engineering Concepts
- Social Engineering Techniques
- Analysis of Insider Threats
- Impersonation on Social Networking Sites
- What is Identity Theft?
- Social Engineering Countermeasures
- Understanding Social Engineering Penetration Testing
- DDoS/DoS Concepts
- DDoS/DoS Attack Techniques
- What is Botnets?
- DDoS Case Studies
- Workings of DDoS/DoS Attack Tools
- DDOS Counter measures
- How to use DDoS/DoS Protection Tools?
- Understanding DDoS/DoS Attack Penetration Testing
- Session Hijacking Concepts
- Understanding Application Level Session Hijacking
- Understanding Network Level Session Hijacking
- Workings of Session Hijacking Tools
- Session Hijacking Countermeasures
- What is Penetration Testing
- Understanding IDS, Firewall, and Honeypot Concepts
- Understanding IDS, Firewall, and Honeypot Solutions
- Concepts of Evading IDS
- How to Evade Firewalls?
- Workings of Firewall/IDS Evading Tools
- Methods of Detecting Honeypots
- Firewall/IDS Evasion Countermeasures
- Penetration Testing
- Web Server Concepts
- Understanding Web Server Attacks
- Web Server Attack Methodology
- Workings of Web Server Attack Tools
- Web server attack Countermeasures
- Patch Management
- Workings of Web Server Security Tools
- What is Web Server Pen Testing?
- Web App Concepts
- Understanding Web App Threats
- Hacking Methodology
- Workings of Web Application Hacking Tools
- Web app hacking Countermeasures
- Workings of Web App Security Testing Tools
- Understanding Web App Pen Testing
- SQL Injection Concepts
- Types of SQL Injection
- SQL Injection Methodology
- Workings of SQL Injection Tools
- Understanding Evasion Techniques
- SQL injection countermeasures
- What are wireless networks
- Fundamentals of wireless terminologies
- Overview of Service Set identifier (SSD)’
- Different types of wireless encryption
- Wi-Fi Authentication Modes
- Several types of wireless antennas
- What are wireless threats
- Introduction to Bluetooth threats
- Bluetooth Hacking Tools
- How to protect against wireless attacks
- Wireless Intrusion Prevention Systems
- Wi-Fi Security Auditing Tools
- Bluetooth Security Tools
- Mobile Platform Attack Vectors
- Analysis of hacking Android OS
- Understanding of hacking iOS
- Using Mobile Spyware
- What is Mobile Device Management?
- Understanding Mobile Security Guidelines and Tools
- What is Mobile Pen Testing?
- IoT Concepts
- Understanding of IoT Attacks
- IoT Hacking Methodology
- Workings of IoT Hacking Tools
- IOT hacking Countermeasures
- Understanding IoT Pen Testing
- Cloud Computing Concepts
- Cloud Computing Threats
- Cloud Computing Attacks
- Analysis of Cloud Security
- Workings of Cloud Security Tools
- Understanding Cloud Penetration Testing
- Cryptography Concepts
- Encryption Algorithms
- Workings of Cryptography Tools
- Overview of Public Key Infrastructure (PKI)
- Detailed understanding of Email Encryption
- Detailed understanding of Disk Encryption
- Cryptanalysis
- Cryptography Countermeasures
Ethical Hacker FAQ’s:
Ethical Hacking is an authorized practice of detecting vulnerabilities in a system or application or company’s infrastructure that bypass system security for identifying potential data breaches and threats in the whole network.
Our expert trainers help you to make a professional resume for job interviews.
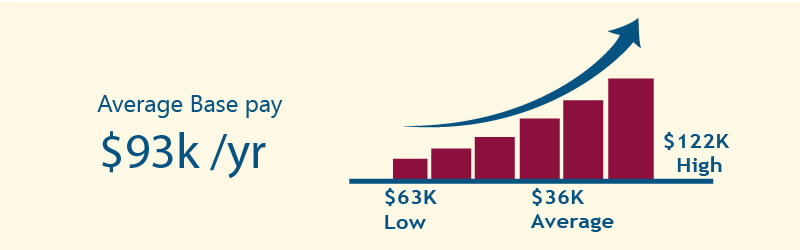
The average salary of certified ethical hacker is $99,658/yr.
The exam format is multiple choice of questions. It is the proctored exam conducted online or at VUE test centres.
Yes, we do provide a certificate upon completion of the course successfully. Our certificate is industry-recognized and will help you gain credibility among the companies hiring.
We would provide you with the missed recording session and also eLearning material for self-study
Yes, you can attend the demo and clear all your hesitations from the experts.
Yes, we do provide job placement services.
Enquire Now
Related Courses
Why PROLOG INFO
Best Virtual training classrooms for IT aspirants
Real time curriculum with job oriented training.
Around the clock assistance
We are eager to solve your queries 24*7 with help of our expert faculty.
Flexible Timings
Choose your schedule as per your convenience. No need to delay your work
Mock projects
Real world project samples for practical sessions



